PC Privacy Cleaner is a fake registry cleaner tool, which pretends to be able to clean your registry.PCPrivacyCleaner may spread with trojans, or you can get duped into downloading PCPrivacyCleaner from PCPrivacyCleaner.com. Once you’ve got PCPrivacyCleaner, it pops up annoying messages and runs fake scans.
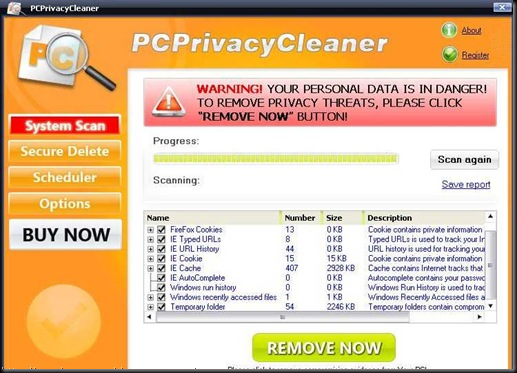
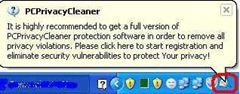
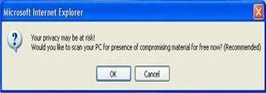
Symptoms
Manual Removal Steps
1.Press Ctrl+Alt+Del to open Task Manager,check any process like pcpc.exe/PCPC_Setup_Free.exe running,kill that process
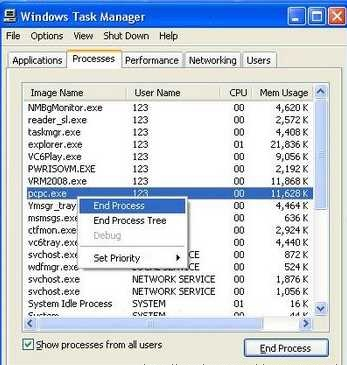
2.Open C:\Program Files (assuming windows installed in C drive) and delete the folder named PCPrivacyCleaner or To find PCPrivacyCleaner directories, go to Start > My Computer > Local Disk (C:) > Program Files > Show the contents of this folder.Search and delete the following PCPrivacyCleaner directories:
C:\ProgramFiles\pcprivacycleaner
%common_programs%\pcprivacycleaner
%program_files%\pcprivacycleaner
3.Remove PC Privacy Cleaner short cuts from desktop, start menu and quick launch.Empty Recycle Bin
4.If PCPrivacyCleaner changed your homepage?Start menu > Control Panel > Internet Options. Next, under Home Page, select the General > Use Default. Type in the URL you want as your home page (e.g., “http://www.google.com”). Then select Apply > OK. You’ll want to open a fresh web page and make sure that your new default home page pops up.
5.How to remove PCPrivacyCleaner registry keys?
Start->Run-> type regedit and press enter.Remove following entries
HKEY_CURRENT_USER\software\pcprivacycleaner
HKEY_CURRENT_USER\software\pcprivacycleaner activationcode
HKEY_CURRENT_USER\software\pcprivacycleaner cookieparams
HKEY_CURRENT_USER\software\pcprivacycleaner installdate
HKEY_CURRENT_USER\software\pcprivacycleaner lastscantime
HKEY_CURRENT_USER\software\pcprivacycleaner totalscancount
HKEY_CURRENT_USER\software\pcprivacycleaner\schedule
HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run pcprivacycleaner HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{70d17a5f-ef27-4295-90f5-20ad6f24834f}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{80ced3d6-ece9-48ba-8df8-2503d8d87c2b}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{aa6d4f53-4c8d-4549-84d2-02d584acc4e9}
6.How to remove PCPrivacyCleaner DLL files
To locate the PCPrivacyCleaner DLL path, go to Start > Search > All Files or Folders. Type PCPrivacyCleaner and in the Look in: select either My Computer or Local Hard Drives. Click the Search button.
Once you have the PCPrivacyCleaner DLL path,Start->Run->type cmd and click “OK.” To change your current directory, type “cd” in the command box, press your “Space” key, and enter the full directory where the PCPrivacyCleaner DLL file is located. (If you’re not sure if the PCPrivacyCleaner DLL file is located in a particular directory, enter “dir” in the command box to display a directory’s contents. To go one directory back, enter “cd ..” in the command box and press “Enter.”)
Here you type regsvr32 /u [dll_name] and press enter to unregister the DLL.If you accidentally do something wrong, you can register it again by using regsvr32 [dll_name].eg:regsvr32 /u pcpc.dll .(How to register/unregister a .dll file)
PCPrivacyCleaner Automatic Removal Instructions
Print these instructions because you’ll have to reboot into Safe Mode. Also back up your computer in case you make a mistake
-
Download and save SmitFraudFix to your desktop.
-
Restart your computer in Safe ModeOnce thedesktop appears, double click on the SmitfraudFix.exe on your desktop.
-
After the credits screen, you’ll see a menu. Select the option number 2, which is ‘Clean (safe mode recommended)’, and thenpress Enter to delete infect files.
-
SmitFraudFix will begin cleaning your computer and take a series of cleanup processes. When the process is over, it will automatically begin the Disk Cleanup program.
-
Once the Disk Cleanup program is complete, you will be prompted with the message ‘Registry cleaning - Do you want to clean the registry’. Answer Y (Yes) and hit Enter. Reboot your computer.
-
SmitFraudFix will now check if wininet.dll is infected. SmitFraudFix will ask you whether to replace the infected file (if there’s any) ‘Replace infected
file?’ Answer by typing Y (Yes) and hit Enter. -
Reboot your computer to complete the cleaning process.
-
After reboot, a Notepad screen may appear containing a log of all the filesremoved from your computer. If it doesn’t appear, a file will be created called rapport.txt in the root of your drive, (Local Disk C:).
-
Restart your computer in Safe Mode .
-
Go to C:\Windows\Temp, click Edit, click Select All, press DELETE, and thenclick Yes to confirm that you want all the items to go to the Recycle Bin.
-
Go to C:\Documents and Settings\[LISTED USER]\Local Settings\Temp, click Edit, click Select All, press DELETE, and then click Yes to confirm that
you want all the items to go to the Recycle Bin. -
Reboot your computer back to normal mode.
How to use SmitfraudFix ,detailed instructions here